Benefits
Control costs of your Clouds
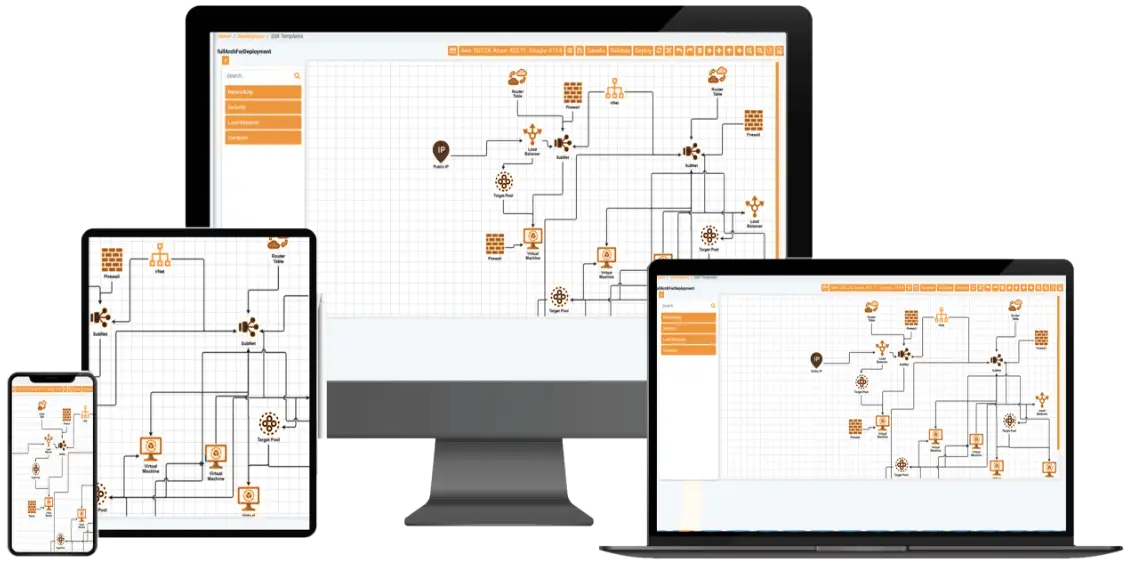
Understanding the cost of your Cloud deployments before you commit to a Cloud. One interface can save time in creating Cloud environments with a policy-controlled Visio-like UI.
Dynamically visualize your cloud infrastructure in real-time. Just draw the cloud agnostic architectures on “Canvas” and deploy on Any cloud with few clicks of button.
From a simple Virtual Machine to complex multi-tiered architecture (Storage, Load Balancers, Firewalls, Route Tables, Disks, etc.) simply draw the architecture and deploy on any Cloud without any changes. No cloud skills required.
Features

Draw Once, Deploy Many
- Re-Use the same architecture for deploying on same or any other cloud of choice with single click of button. No cloud skills required.
- Provision IaaS and PaaS service on AWS, Azure and Google
- Migrate workloads 10x faster and achieve economies of scale
- Realize Higher ROI in lesser time
- Let your team focus on real business problem while our Canvas tool takes care of provisioning on any public cloud.

Policies Enforce Controls
Object Policies are essential for ensuring that cloud deployments meet stringent security controls and comply with industry or government regulations. Here are some key aspects:
- Access Control: Object Policies help define who can access specific data and what actions they can perform, ensuring only authorized users have access.
- Data Encryption: Policies can enforce encryption standards for data at rest and in transit, protecting sensitive information from unauthorized access.
- Audit and Monitoring: They enable detailed logging and monitoring of access and changes to data, which is crucial for compliance and security audits.
- Data Retention and Deletion: Policies can specify how long data should be retained and when it should be deleted, helping to comply with regulations like GDPR or HIPAA.
- Compliance Frameworks: Object Policies can be tailored to meet specific compliance frameworks such as ISO 27001, NIST, or FedRAMP, ensuring that your cloud deployment adheres to required standards.

AI-Enabled Mitigation
AI-powered cloud security is indeed a game-changer! By leveraging AI, cloud environments can detect and respond to threats in real-time, often before they cause significant damage. The ability to move your workload to another Cloud in 11 minutes or less!

Validate Your Workload
Using a drag-and-drop interface to create environments and workloads simplifies the process significantly, making it accessible even for those who might not be deeply technical.
Once the workload is created, AI validation ensures that everything is configured correctly and securely before deployment. This step can catch potential issues early, reducing the risk of errors or vulnerabilities. Finally, deploying with a single click makes the entire process efficient and user-friendly.
This approach not only saves time but also enhances security and reliability. Are you considering implementing such a solution, or are you exploring options for your current cloud setup?