Benefits
Controlling Movement
Blocking lateral movement and preventing malware from entering through user clicks are crucial steps in enhancing your cybersecurity posture.
Features

Verify Privileged User Access
Verifying privileged access users before tasks are executed is crucial for preventing lateral movement within a network. Here are some effective strategies:
- Multi-Factor Authentication (MFA): Implement MFA for all privileged access. This ensures that even if an attacker obtains a user’s credentials, they cannot gain access without the second form of verification.
- Privileged Access Management (PAM): Use PAM solutions to monitor and control privileged accounts. These tools can enforce just-in-time access, where privileges are granted only for the duration of a specific task.
- Role-Based Access Control (RBAC): Assign roles based on the principle of least privilege, ensuring users have only the access necessary to perform their tasks.
- Network Segmentation: Isolate critical systems and sensitive data to limit the potential impact of a compromised account.
- Regular Audits and Monitoring: Continuously monitor and audit privileged access activities to detect and respond to suspicious behavior promptly.

Geofence Service Accounts
Geofencing service accounts to specific servers is an effective strategy to limit data exfiltration and reduce risk. Here are some steps to achieve this:
- Geofencing: Restrict service accounts to specific geographic locations or IP ranges. This ensures that the accounts can only access the servers they need, reducing the risk of unauthorized access.
- Network Segmentation: Isolate critical systems and sensitive data by segmenting your network. This limits the movement of service accounts and reduces the potential impact of a compromised account.
- Access Controls: Implement strict access controls to ensure that service accounts have the minimum necessary permissions. This follows the principle of least privilege, reducing the risk of data exfiltration.
- Monitoring and Auditing: Continuously monitor and audit the activities of service accounts. Use tools like Microsoft Defender for Cloud Apps to detect and prevent malicious behavior.
- Endpoint Protection: Deploy advanced endpoint protection solutions to detect and block malware before it can execute. This helps prevent service accounts from being used to exfiltrate data.
Are you looking to implement these measures in your current setup, or are you exploring options for a new project?

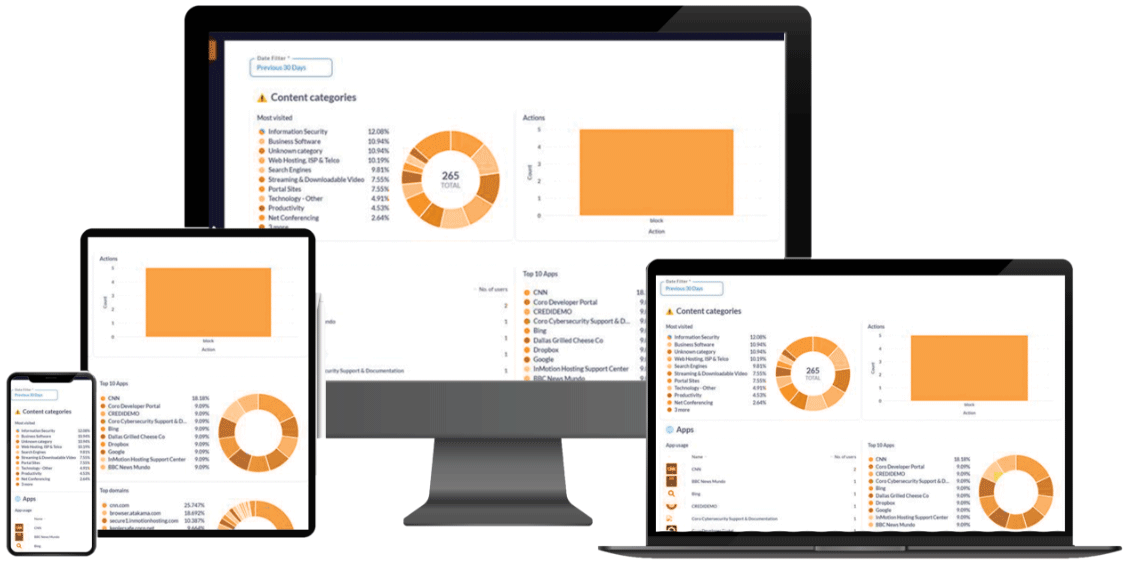
Secure Website Access
Implementing role-based access control (RBAC) to secure website access and limit distractions is a smart approach. Here’s how you can achieve this:
- Role-Based Access Control (RBAC): Assign permissions based on the roles within your organization. Each role will have access only to the websites and resources necessary for their job.
- User Education: Train users on the importance of adhering to access policies and the risks associated with visiting unauthorized websites.
- Monitoring and Auditing: Continuously monitor web access and audit logs to detect and respond to any unauthorized access attempts.

Prevent Malicious Site Access
Preventing ransomware by blocking malicious links is crucial for maintaining a secure environment. Here are some effective strategies to achieve this:
- URL Filtering: Implement URL filtering to block access to known malicious websites. This can be done using security solutions like Secure Web Gateways (SWG) or DNS filtering.
- Email Security: Use email security solutions that scan and filter out emails containing malicious links or attachments. This helps prevent phishing attacks that often lead to ransomware infections.
- Browser Isolation: Employ browser isolation techniques to open potentially risky websites in a secure, isolated environment. This prevents any malicious code from reaching the user’s device.
- Endpoint Protection: Deploy advanced endpoint protection solutions that can detect and block malicious links before they are clicked. These solutions often include real-time scanning and behavior analysis.
- User Training: Educate users about the dangers of clicking on unknown links and how to recognize phishing attempts. Regular training can significantly reduce the risk of ransomware infections.
- Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security. Even if a user clicks on a malicious link, MFA can prevent unauthorized access to sensitive systems.
Are you looking to implement these measures in your current setup, or are you exploring options for a new project?